Over the past decade, hotels have rapidly integrated technology into nearly every facet of operations. This has brought unparalleled efficiencies and connectivity, but it has also exposed hotels to a growing number of cybersecurity threats.
While cyberattacks on major hotel brands make headlines, the hospitality sector as a whole is vulnerable. According to a Trustwave report, nearly 31% of hospitality organizations have reported a data breach in their company’s history. Of these, almost 90% were affected more than once in a year—indicating that falling victim once increases the likelihood of being targeted again.
31%
of hospitality orgs have reported a data breach
90%
of these were affected more than once/year
Why are hotels such prime targets? Cybercriminals are after sensitive guest information—including credit card details, passport numbers, and personally identifiable information (PII)—which they can sell, hold for ransom, or use in fraudulent financial transactions.
Claudia Infante, Chief Data Officer at Margaritaville, shared that keeping guest data safe and secure is one of the most pressing concerns she deals with during an episode of The Turndown, saying, “The more you start threading technology, the more doors you open for your data to be compromised.”
Tune in to The Turndown.
Listen to Claudia Infante, Chief Data Officer at Margaritaville.
Below, we break down some of the most common cybersecurity scams in hospitality, how they work, and how hoteliers can mitigate risk through better cybersecurity practices.
1. Phishing emails
Cyber threats often begin with a simple email. In a phishing attack, hackers impersonate vendors, online travel agencies (OTAs), or even executives to trick employees into clicking malicious links, downloading malware, or revealing login credentials.
In 2023, cybersecurity researchers at FortiGuard Labs uncovered a phishing campaign in which attackers sent emails posing as hotel reservation inquiries. The emails contained malicious PDF attachments that, when opened, executed the “MrAnon Stealer” malware, which was capable of extracting sensitive customer data from the system.
To protect your hotel from phishing emails:
- Train staff to verify sender domains and never click suspicious links
- Use email authentication and spam filters
- Promote a “stop and check” culture across teams handling guest data and financial information
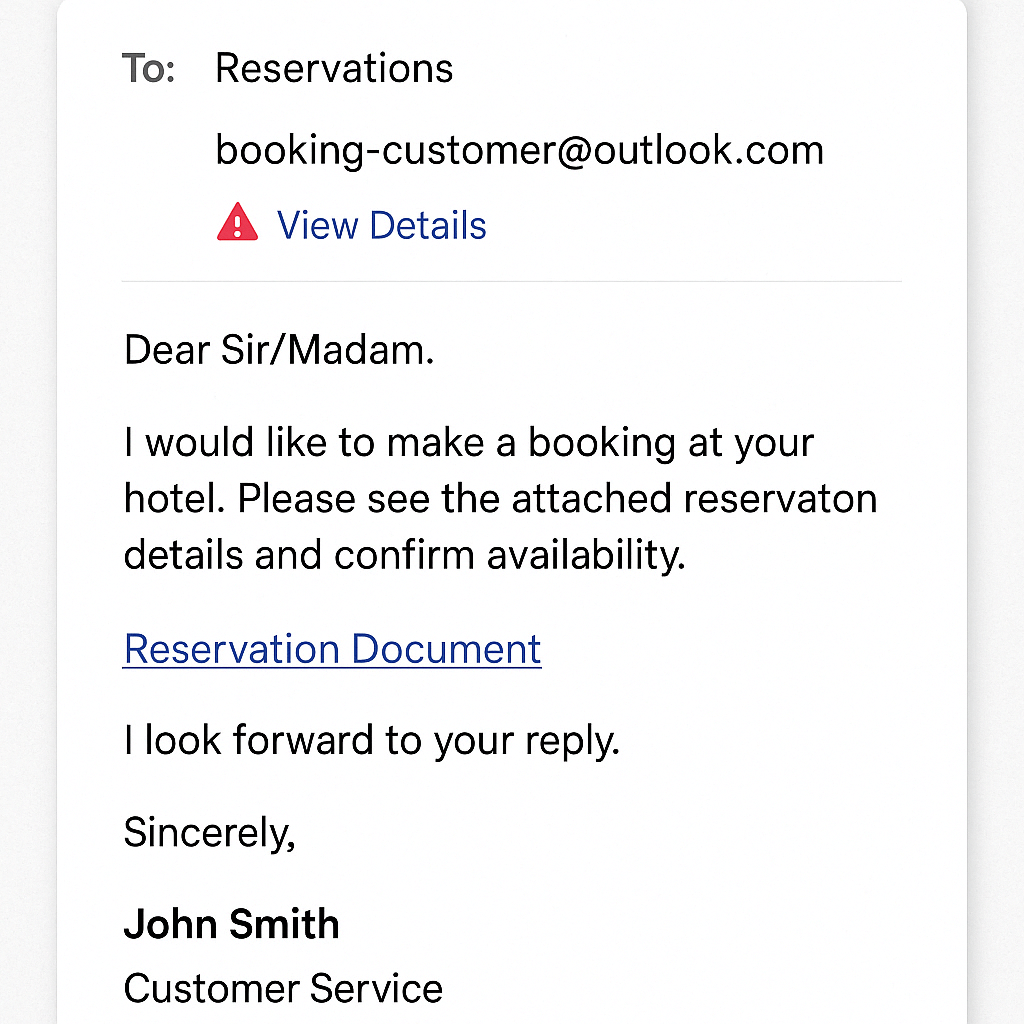
2. Fake OTA booking scams
A form of phishing is OTA booking scams, targeting both hotel employees and guests. Guests receive fake emails or texts impersonating platforms like Booking.com or Expedia, asking them to reconfirm or re-pay for a booking. These often link to spoofed sites that steal payment data. Hotel employees, meanwhile, may receive fake OTA booking confirmation emails or warnings designed to trick them into clicking malware-laced links under time pressure.
In 2023, the Australian Competition and Consumer Commission reported a 580% surge in scams related to Booking.com, with losses surpassing $337,000. Scammers sent phishing emails to hotel partners, leading to unauthorized access and impersonation, allowing fraudsters to contact guests directly and request payment methods.
580%
surge in scams related to Booking.com
To protect your hotel and guests from OTA booking scams:
- Educate guests in pre-arrival emails that you will never request payment via text or third-party links
- Bookmark OTA login pages and avoid using search engines to access them
- Train staff to verify sender addresses and respond only through official platforms
- Enable multifactor authentication for OTA extranets and PMS logins
- Report suspicious emails or impersonation attempts to OTA partners immediately
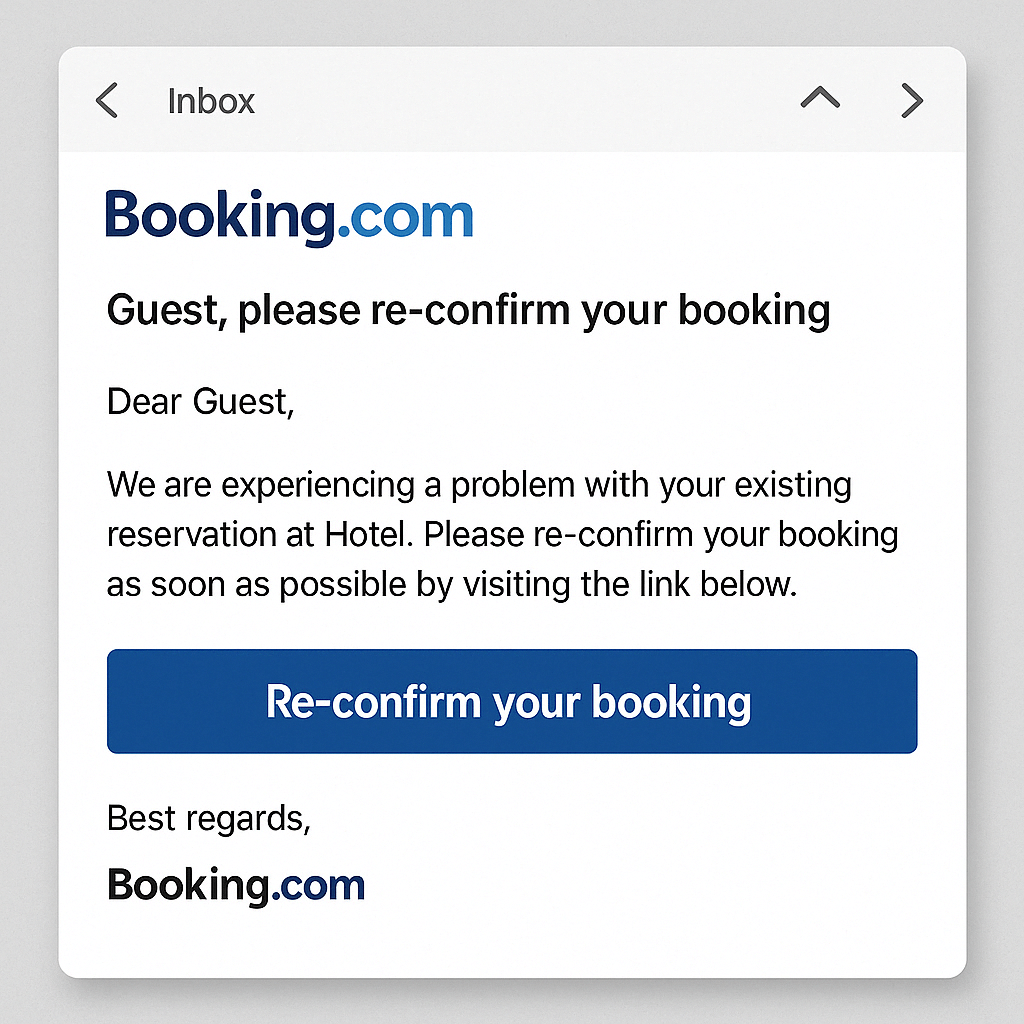
3. Vishing (voice phishing)
Like phishing, but over the phone—vishing involves scammers impersonating hotel executives, IT support, or even banks to trick staff into sharing sensitive information.
In September 2023, MGM Resorts was hit with a vishing attack where a hacker impersonated an employee to gain internal access to critical systems. The breach led to widespread outages, affecting hotel room locks, payment systems, and digital booking tools.
To protect your hotel from vishing:
- Train staff to be wary of unexpected or urgent calls requesting information
- Never provide passwords or sensitive information over the phone
4. Credential stuffing
Credential stuffing involves using stolen usernames and passwords—often obtained from unrelated breaches—to gain access to internal systems or administrative networks. If staff reuse passwords or store them insecurely, the risk increases significantly.
In 2020, Marriott confirmed a breach in which attackers used credential stuffing to access stolen data from approximately 5.2 million guests. Ameet Naik, Security Evangelist at PerimeterX, says, “Eventually hackers find a username and password that works that will let them buy goods for resale, drain loyalty accounts, or steal personal information.”
To protect your hotel from credential stuffing:
- Enforce strong, unique passwords for every system
- Enable two-factor authentication (2FA) wherever possible
- Use role-based access control (RBAC) in your PMS to limit data exposure
- Monitor new device login notifications for possible unauthorized access
- Implement single sign-on (SSO) where possible to reduce password fatigue
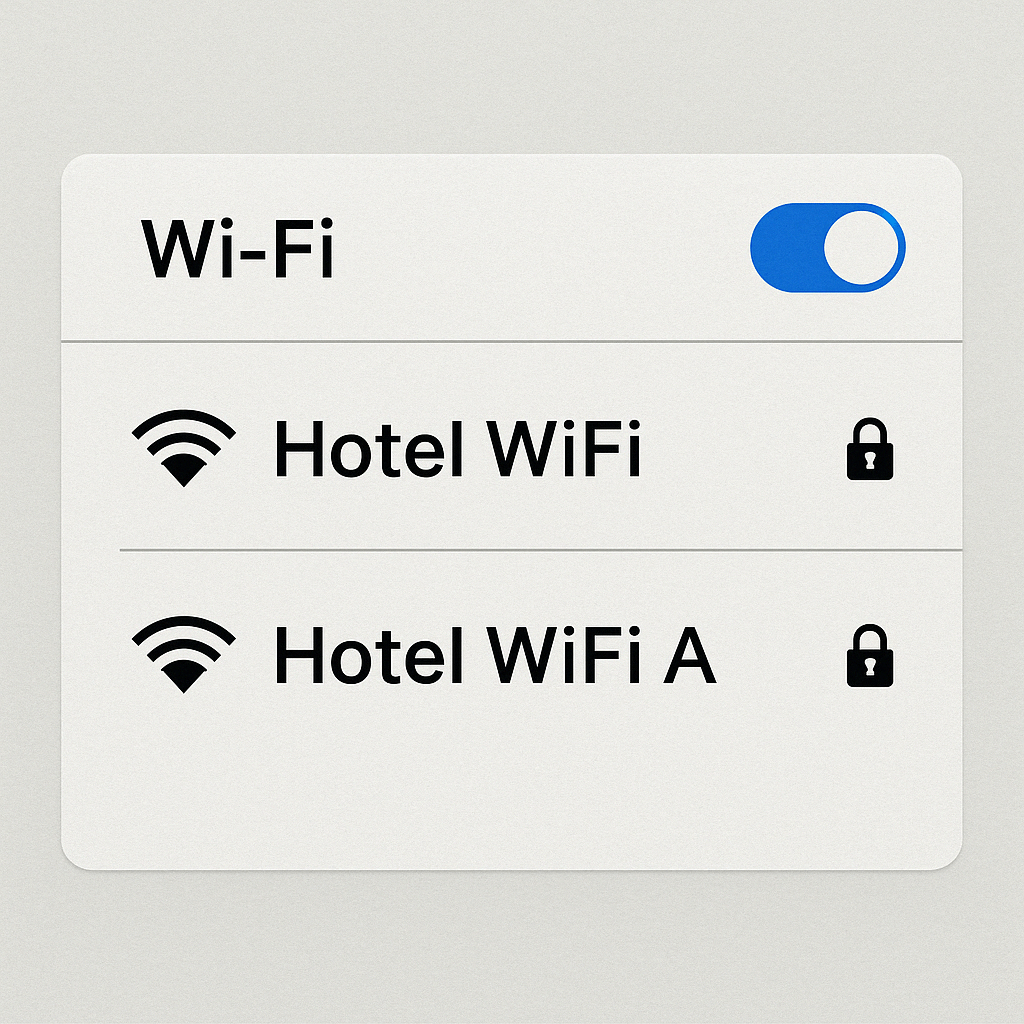
5. Wifi spoofing
Wifi spoofing occurs when scammers create rogue Wi-Fi networks that appear nearly identical to your hotel’s, tricking guests into connecting. These networks can intercept traffic, capture logins, or install malware.
The “DarkHotel” cyber-espionage campaign targeted business travelers by compromising hotel Wi-Fi networks. Attackers uploaded malicious code to hotel servers, allowing them to target specific users who were guests at luxury hotels, primarily in Asia and the United States.
To protect your hotel from wifi spoofing:
- Clearly communicate the official wifi network name to guests at check-in
- Use WPA2 or WPA3 encryption on all networked devices
- Monitor for rogue access points with wireless intrusion detection systems
6. Keycard vulnerabilities
Cybercriminals and researchers alike have shown how flaws in outdated keycard systems can allow unauthorized room access using RFID cloning tools or firmware exploits.
In one well-known example, a group of security researchers revealed a hotel keycard hacking technique called ‘Unsaflok’ that allowed them to almost instantly open several models of keycard locks, which were installed on 3 million doors worldwide.
To protect your hotel from keycard hacks:
- Ensure locks are up-to-date with the latest firmware
- Avoid generic master keys or hardcoded credentials
- Work with lock providers that support remote auditing and real-time alerts
7. Overpayment scams
Overpayment scams involve using a credit card to “overpay” for a booking (often with a stolen card or fake virtual card) and then requesting a refund via a different payment method, usually before the original charge is flagged as fraudulent.
These scams exploit the complexity of credit card workflows and payment reversals, especially for hotels managing multiple payment methods.
To protect your hotel from overpayment scams:
Payments shouldn’t be a source of stress.
Follow these SOPs to avoid payment scams at your property.
8. Friendly fraud (chargeback fraud)
Friendly fraud occurs when a guest disputes a legitimate charge, often falsely claiming they never stayed or authorized the payment. This can be especially harmful for non-refundable bookings, group blocks, or special event stays.
Sift’s Digital Trust & Safety Index found that 17% of consumers who filed chargebacks admitted to doing so fraudulently.
To protect your hotel from chargeback fraud:
- Collect and store signed registration cards or digital check-in confirmations
- Use clear, consistent billing descriptors so guests recognize charges
- Document all guest interactions, especially around refunds or complaints
- Fight chargebacks with PMS and payment processing tools that offer dispute resolution workflows (like Cloudbeds’ dispute portal)
Staying one step ahead
The hospitality industry relies on guest trust—and today’s cybersecurity challenges are testing that trust more than ever. From stolen customer information to compromised reservation systems, hotels face an expanding attack surface that requires continuous vigilance.
The good news? These cybersecurity risks are largely preventable.
By fostering a strong cybersecurity culture, investing in secure IT infrastructure, and collaborating with third-party vendors who take data protection seriously, hotels can safeguard guest experiences, protect financial data, and avoid the legal, reputational, and financial implications of a breach.
Peace of mind, built in.
Cloudbeds checks all the boxes on global security standards.



